For most of the morning, researchers believed the ransomware to be a variant of Petya, but Kaspersky Labs and others are reporting that, though it has similarities, it’s actually #NotPetya. Regardless of its name, here’s what you should know. Petya is a piece of ransomware that infects computers with the intent of monetary extortion in return for access to the contents of the PCs. It encrypts files, claiming only to let you back in. Patch your Windows systems to remove one attack vector for Petya Ransomware. It is critial that you address Microsoft Security Bulletin MS17-010 and patch all Windows clients on your network. Microsoft have published a good post at this link which more background on this and also includes some information on what they are doing to prevent the spread of this Ransomware.
As happened recently with WannaCrypt, we again face a malicious attack in the form of ransomware, Petya. In early reports, there was a lot of conflicting information reported on the attacks, including conflation of unrelated and misleading pieces of data, so Microsoft teams mobilized to investigate and analyze, enabling our Malware Protection team to release signatures to detect and protect against the malware.
Based on our investigation, the malware was initially delivered via a Ukrainian company’s (M.E.doc) update service for their finance application, which is popular in Ukraine and Russia. Once the initial compromise took hold, the ransomware used multiple tools in its arsenal to spread across impacted networks. If unpatched, the malware uses vulnerabilities CVE-2017-0144 and CVE-2017-0145 to spread across networks. Microsoft released MS17-010 in March that addressed the vulnerabilities exploited by Petya. If that technique was not effective, the malware uses other methods like harvesting of credentials and traversing networks to infect other machines. (read the Microsoft Malware Protection Center analysis here for more details.)
We recommend customers that have not yet installed security update MS17-010 to do so as soon as possible. If for some reason you cannot apply the update, we recommend a possible workaround to reduce the attack surface: disable SMBv1 with the steps documented at Microsoft Knowledge Base Article 2696547. In addition, consider implementing techniques like network segmentation and least privileged accounts that will further limit the impact of these types of malware attacks. For those using Windows 10, leverage capabilities like Device Guard to lock down devices and allow only trusted applications, effectively preventing malware from running. Finally, consider leveraging Windows Defender Advanced Threat Protection, which automatically detects behaviors used by this new ransomware.
The last few months has illustrated that in today’s threat landscape, cybercriminals will continue to alter their attacks and defending against this requires an equal amount of vigilance and effort. Microsoft is committed to working with partners and customers to combat the malicious efforts of these criminals.
We are continuing to investigate and will take appropriate action to protect customers.
Phillip Misner, 7778: the nemesis parts 12 gauge.
Principal Security Group Manager
More Resources:
MMPC blog: https://blogs.technet.microsoft.com/mmpc/2017/06/27/new-ransomware-old-techniques-petya-adds-worm-capabilities/
Next-generation ransomware protections with Windows 10 Creators update: https://blogs.technet.microsoft.com/mmpc/2017/06/08/windows-10-creators-update-hardens-security-with-next-gen-defense/
Petya Ransomware Download For Testing
Microsoft Malware Encyclopedia post on Petya: https://www.microsoft.com/en-us/security/portal/threat/encyclopedia/Entry.aspx?Name=Ransom:Win32/Petya
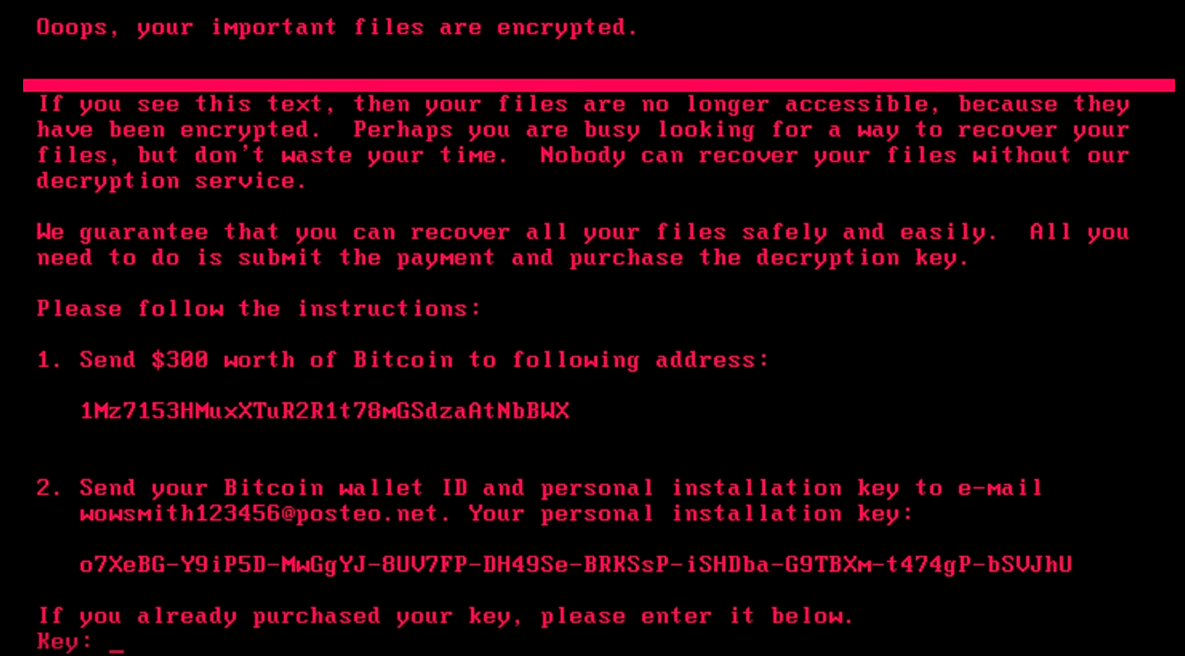
When it comes to ransomware, this sophisticated piece of malware that blocks the victim’s access to his/her files until a ransom is paid, Petya ransomware is surely one that has stirred up some nuisances.
What is Petya Ransomware, You May Wonder?
Petya ransomware actually represents a family of ransomware that affects Microsoft Windows-based components. When a computer’s master boot record is infected with Petya, it executes a payload that encrypts data on the hard drive’s systems. Petya can lock up the entire hard drive, preventing the computer from booting up completely.
Petya Ransomware – History
Petya ransomware, whose name is a GoldenEye 1995 James Bond movie reference, firstly appeared in 2016, when it used to spread via malicious email attachments.
Petya ransomware became famous in 2017, though, when a new variant, which can be found in the press with the name NotPetya, hit Ukraine. As Microsoft says, in Ukraine “more than 12,500 machines encountered the threat.” They “then observed infections in another 64 countries, including Belgium, Brazil, Germany, Russia, and the United States.”
Petya Ransomware – How Does It Work?
Petya ransomware encrypts a computer’s Master File Table (MFT), which acts like a quick-reference guide for all the files located on the drive. By being unable to access the MFT, the computer won’t find any files, so it won’t boot up.
After Petya ransomware gets installed on the computer, it proceeds with infecting the Master Boot Record (MBR) – that computer part that loads the operating system when the computer is turned on. The process goes as follows: Petya forces the computer to restart and then the ransom note is displayed while the MFT is being encrypted. The infected computer won’t be able to access anything on its hard drive – not even its operating system.
Petya ransomware usually spreads via email campaigns in which there are various types of attachments – .zip, .exe, .pdf, .pif etc. – or various links to online services. The fake emails pattern upon job offers, job applications or legal proceedings and rely on the user to run the compromised attachments.
Petya ransomware might also propagate itself by exploiting the MS17-010 vulnerability (EternalBlue) or by getting access to credentials and spreading across network shares. EternalBlue “is the name given to a software vulnerability in Microsoft’s Windows operating system” and it works by “exploiting the Microsoft Server Message Block 1.0. The SMB is a network file sharing protocol and <<allows applications on a computer to read and write to files and to request services>> that are on the same network.”
Petya Ransomware – What about NotPetya?
NotPetya exploits the EternalBlue vulnerability and is even more dangerous than Petya ransomware because it permanently encrypts any file it finds. In case of a NotPetya attack, decryption is impossible even if the victim decides to pay the ransom. For this reason, NotPetya can be considered a wiper malware disguised as ransomware.
Petya Ransomware – Famous Targets
Petya Ransomware Removal
The most famous target of the Petya / NonPetya Ransomware was Ukraine, although similar attacks were reported in Russia, Polland, France, Germany, Italy, United Kingdom, United States and Australia.
The 2017 attack is believed to have “originated from an update of a Ukrainian tax accounting package called MeDoc […], developed by Intellect Service. MeDoc is widely used among tax accountants in Ukraine, and the software was the main option for accounting for other Ukrainian businesses, according to Mikko Hyppönen, a security expert at F-Secure.MeDoc had about 400,000 customers across Ukraine, representing about 90% of the country’s domestic firms and prior to the attack was installed on an estimated 1 million computers in Ukraine.”
On the 27th of June, the day of the attack, a MeDoc update was released – and then the ransomware notes began to appear. Marcus Hutchins, a British malware expert, believes that “the software’s automatic update system was compromised and used to download and run malware rather than updates for the software.”
Petya Ransomware Attack
NotPetya encrypted all the files found on the infected machines and could also intercept passwords and perform administrator-level actions.
Among the institutions that were affected by the $10 billion attack(s) (total damage) there were Ukraine’s Chernobyl Nuclear Power Plant, various Ukrainian ministries, banks and metro systems, as well as the Boryspil International Airport, Ukrposhta and Ukrain Railways.
Outside Ukraine, some of the victims were: the Danish shipping firm Maersk, the Russian oil company Rosneft, the American pharmaceutical giant Merck.
Petya Ransomware – Prevention Strategies
As we have seen, Petya is a dangerous type of ransomware and its variant, NonPetya, is even more dangerous because the data it encrypts remains lost or compromised even if the ransomware is paid. Speaking of paying the ransom… our advice for you is certain: don’t. Just as the FBIsays,
In some cases, victims who paid a ransom were never provided with decryption keys. In addition, due to flaws in the encryption algorithms of certain malware variants, victims may not be able to recover some or all of their data even with a valid decryption key. Paying ransoms emboldens criminals to target other organizations and provides an alluring and lucrative enterprise to other criminals. However, the FBI understands that when businesses are faced with an inability to function, executives will evaluate all options to protect their shareholders, employees, and customers. Regardless of whether you or your organisation have decided to pay the ransom, the FBI urges you to report ransomware incidents to law enforcement. Doing so provides investigators with the critical information they need to track ransomware attackers, hold them accountable […], and prevent future attacks.
Here’s what measures you can adopt in order to prevent a Petya ransomware attack:
Make sure all your data have backups
This might be the most important security measure anyone can take to make sure they never lose access to their data. You can find some more advice on this subject here.
Update and patch everything
The operating systems and all the software your company uses should be up to date and patched on time on all your devices. To simplify your mission, we have created a patch management solution for Windows and 3rd party software – X-Ploit Resilience. Our solution will help you deploy Windows, 3rd party and custom software to your endpoints anywhere in the world, allowing you to schedule updates at your convenience or push them immediately with zero user interruption.
Invest in professional cybersecurity solutions
Any company needs an antivirus solution as a first step of a cybersecurity strategy. If you’re interested in finding a next-generation antivirus, you could try our Thor Vigilance Enterprise. Thor Vigilance Enterprise uses DNS filtering to block ransomware, spyware and riskware and monitors all processes in order to detect and identify known and unknown threats.
Be careful with admin privileges

Admin privileges refer to the management of privileged accounts. Privileged accounts are those accounts that have the most power inside an IT department and are used by the team to set up the IT infrastructure, to install new software or hardware, to run critical services or to conduct maintenance operations – local administrative, domain administrative, service accounts. To put it simply, privileged accounts can access an organization’s highly classified IT assets and the sensitive information stored within them.
On that score, our Season 3. Privileged Access Management solution can help you remove permanent rights and give rights when needed for the period that they’re necessary and the rights granted can be revoked any time, while all actions will be logged for a full audit trail.
System admins waste 30% of their time manually managing user rights or installations.
which frees up huge chunks of sys-admin time.
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
Train all your employees
There used to be a cyber joke that said: in this corner of the ring we have firewalls, encryption, antivirus software etc. In the opposing corner of the ring we have Dave (who was wearing a T-shirt which read “human error”). It could not be more true: you can have backups and all the proper solutions set in place – human error is still possible and very much exploited by cybercriminals.
Make sure your people know what to do, what not to do, how to avoid ransomware and how to report it if it happens. It’s also important that they know they should never try to pay the ransom on their own.
If you will be unfortunate enough to become the victim of a ransomware attack, you should:
– turn computers off and disconnect from the network;
– notify the proper authorities;
– try to detect who and what in your network has been compromised;
– formulate a response;
– don’t rely solely on free decryption tools.
Wrapping Up
Even though ransomware already has a long history and there were thousands of targets around the Globe, it is still one of the most high-profile forms of cyberattack. It’s important to remember that paying the ransom only seems the quickest and easiest way of getting back in business, so you must have some security measures in place in order to avoid an attack in the first place.
However you choose to proceed, please remember that Heimdal™ Security always has your back and that our team is here to help you protect your home and your company and to create a cybersecurity culture to the benefit of anyone who wants to learn more about it.
Drop a line below if you have any comments, questions or suggestions – we are all ears and can’t wait to hear your opinion!